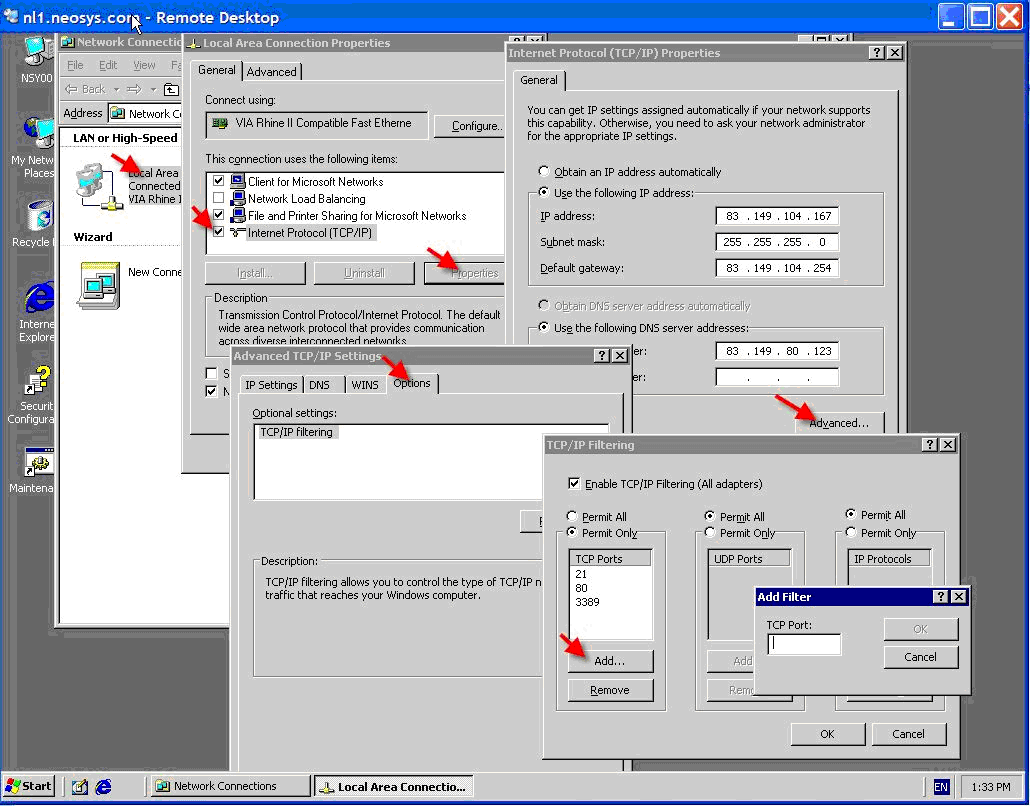
Setting up TCP/IP filtering
From NEOSYS Technical Support Wiki
Jump to navigationJump to search
Tcp/ip filtering is a simple but effective firewall but cannot distinguish between incoming and outgoing traffic or do port forwarding.
All dedicated Neosys client servers which are installed in future will have TCP/IP filtering enabled and we will drop installation of anti-virus programs. However it the client has a workgroup anti-virus installation than it can be installed in addition to TCP/IP filtering.
Note:
- Despite Windows telling you that it is necessary to reboot to activate any changes, it is probably NOT necessary.
- Don't do changes while critical users are working or you cannot get power cycle the server since changing filtering sometimes causes network failure.
The following ports need to be opened when TCP/IP filtering is enabled:
- 80/8123 web
- 443/4430 secure web
- 22/19580 ssh
- 25/2500 smtp
- 5500/55000 vnc reverse connection
and optionally
- 3389/33890 rdc
- 5900/59000 vnc
On our own NEOSYS server, some standard ports which need to be opened:
- 21 standard ftp
- 80 standard http
- 443 standard https
- 3389 standard remote desktop connection
NEOSYS non-standard ports
- 2500 neosys smtp
- 4430 neosys https port
- 55000 neosys ultravnc reverse connection
- 19580 neosys ssh port
- 8000 neosys wiki
TCP/IP properties, advanced, options