Setting up TCP/IP filtering: Difference between revisions
From NEOSYS Technical Support Wiki
Jump to navigationJump to search
No edit summary |
No edit summary |
||
| Line 1: | Line 1: | ||
Tcp/ip filtering is a simple but effective firewall but | Tcp/ip filtering is a simple but effective firewall but only blocks incoming ports and not outgoing ports. All dedicated Neosys client servers need to have TCP/IP filtering enabled and we will drop installation of anti-virus programs. However it the client has a workgroup anti-virus installation than it can be installed in addition to TCP/IP filtering. | ||
All dedicated Neosys client servers | |||
Note: | Note: | ||
# | #Reboot is necessary for changes to be effective. | ||
#Don't do changes either a) while critical users are working or b) you cannot get to power cycle the server. Changing filtering sometimes causes network failure requiring manual intervention. | #Don't do changes either a) while critical users are working or b) you cannot get to power cycle the server. Changing filtering sometimes causes network failure requiring manual intervention. | ||
The following ports need to be opened when TCP/IP filtering is enabled: | The following ports need to be opened when TCP/IP filtering is enabled for client servers: | ||
*2500 | *80 | ||
*4430 | *443 | ||
*55000 | *2500 | ||
* | *3389 | ||
* | *4430 | ||
*19580 | |||
*55000 | |||
*55001 | |||
*55002 | |||
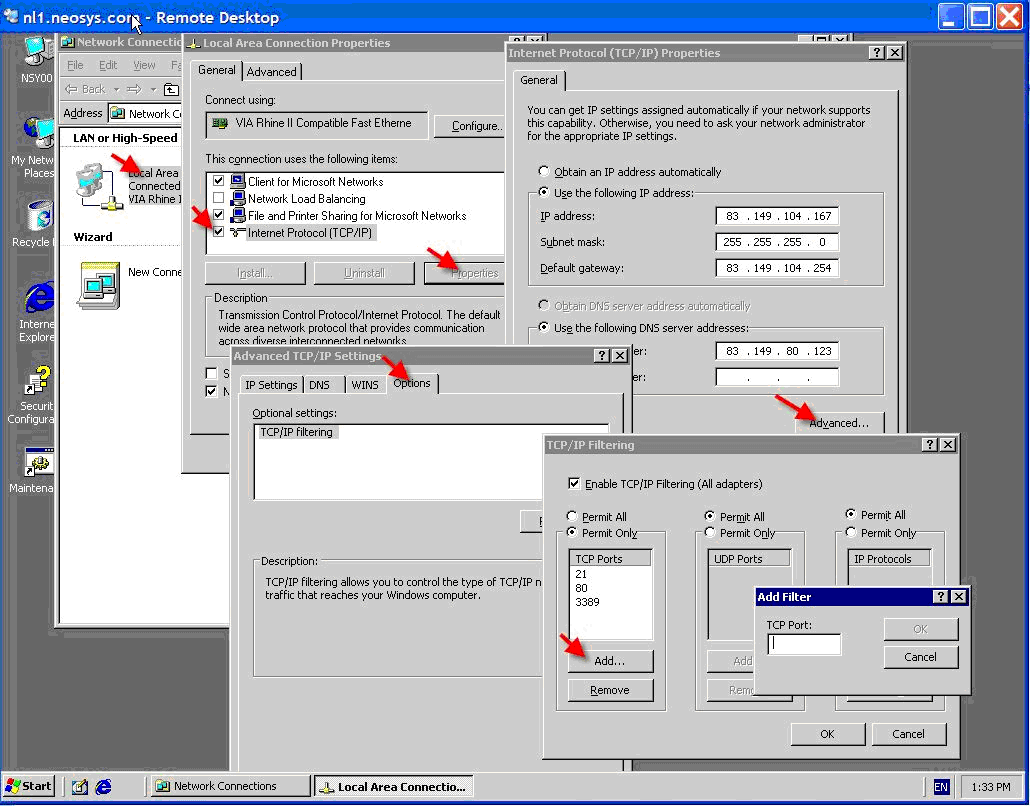
TCP/IP properties, advanced, options | TCP/IP properties, advanced, options | ||
[[Image:tcpipfiltering1.png]] | [[Image:tcpipfiltering1.png]] | ||
Revision as of 08:21, 11 February 2010
Tcp/ip filtering is a simple but effective firewall but only blocks incoming ports and not outgoing ports. All dedicated Neosys client servers need to have TCP/IP filtering enabled and we will drop installation of anti-virus programs. However it the client has a workgroup anti-virus installation than it can be installed in addition to TCP/IP filtering.
Note:
- Reboot is necessary for changes to be effective.
- Don't do changes either a) while critical users are working or b) you cannot get to power cycle the server. Changing filtering sometimes causes network failure requiring manual intervention.
The following ports need to be opened when TCP/IP filtering is enabled for client servers:
- 80
- 443
- 2500
- 3389
- 4430
- 19580
- 55000
- 55001
- 55002
TCP/IP properties, advanced, options