Setting up HTTPS: Difference between revisions
No edit summary |
|||
| (80 intermediate revisions by 12 users not shown) | |||
| Line 1: | Line 1: | ||
== | == Setting up HTTPS for NEOSYS website == | ||
CAUTION: When importing certificates on servers that are not owned by NEOSYS you MUST NOT check the "allow certificate export" option otherwise anybody with access to the server can steal the NEOSYS certificate and pass off their own servers as NEOSYS certified. | |||
NEOSYS has a very simple way of enabling https for all the clients. Every client has been set up with domain name " *.hosts.neosys.com " where "*" is the clientname. | |||
Pre prepared certificate for *.hosts.neosys.com web sites is present on the nl10r/win3 server. The certificate is signed by COMODO and supports SHA2 security algorithm. It is portable, ensures authenticity and is widely supported. Also refer to [http://itwiki.neosys.com/index.php/SSL_certificate SSL certificate] | |||
If a client's URL is not as per NEOSYS standards, but has been in use for many years, do not change the URL without a good enough reason. | |||
=== Creating a single HTTPS web site on Windows 2008 === | |||
To create a single HTTPS web site on Windows 2008, follow three simple steps: | |||
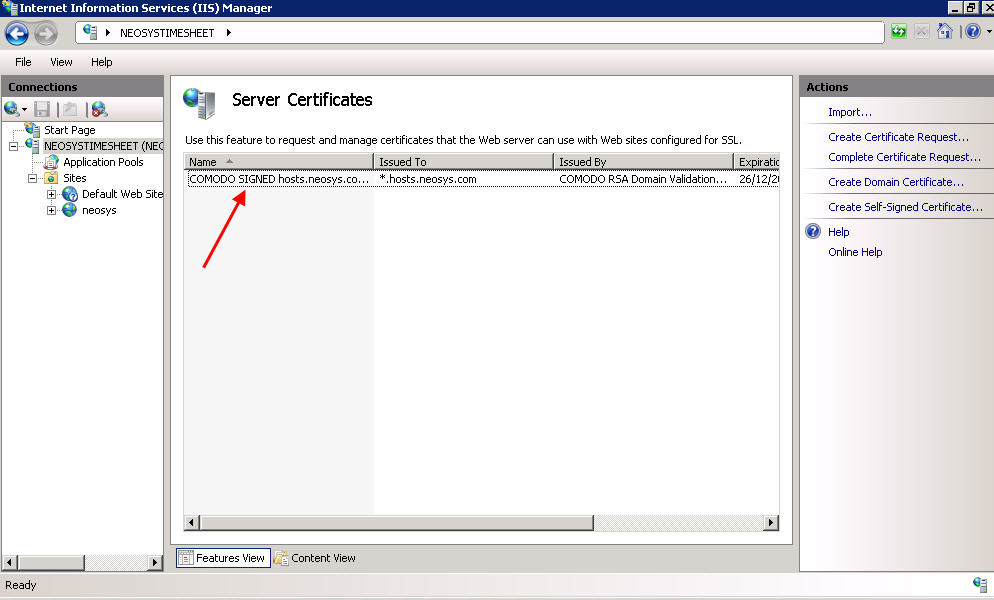
#Copy the "*.hosts.neosys.com.pfx" certificate saved in d:\hosts\certificates on win3 to the server (password to be used is present in a text file in the same folder). | |||
#Import the certificate to IIS without option to export and MUST be deleted after import. See [http://techwiki.neosys.com/index.php/Setting_up_HTTPS#Steps_to_follow_while_importing_certificate_and_why Importing certificate in IIS] for details. | |||
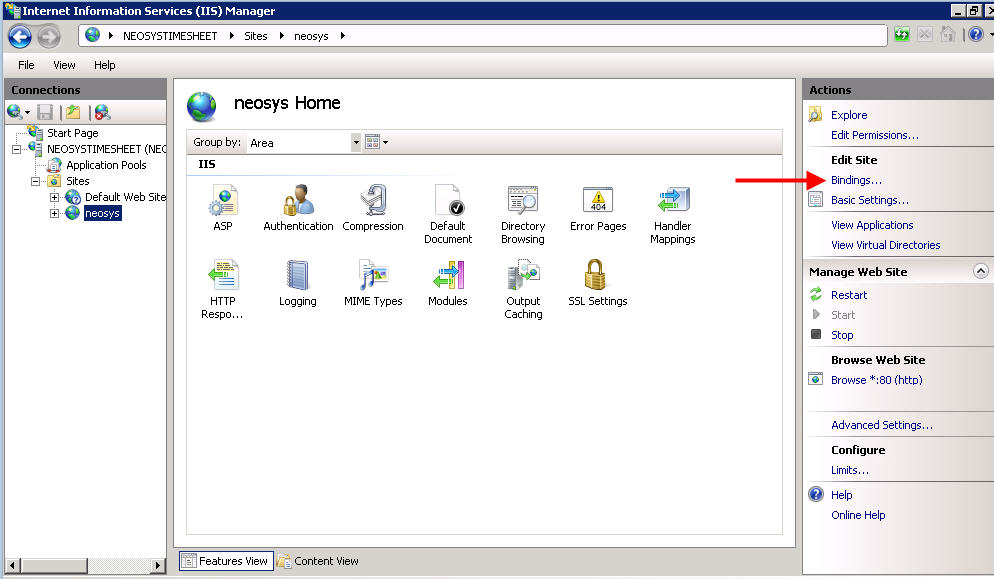
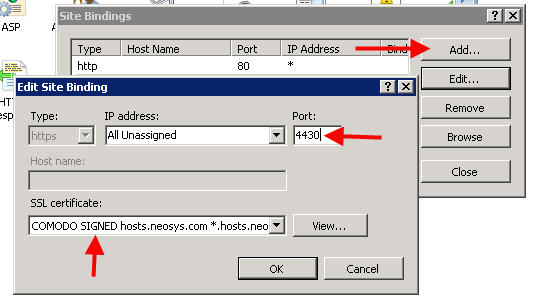
#Click on Sites > Client Web Site > Bindings. In the Bindings section - click on Add and select https, All Unassigned IP addresses, port 4430 and select the certificate from the drop down and click OK. | |||
[[image:sslwin2008-2.jpg]] | |||
[[image:sslwin2008-3.jpg]] | |||
[[image:sslwin2008-4.jpg]] | |||
Test the site from explorer to make sure it works. | |||
=== | === Creating a single HTTPS web site on Windows 2003 === | ||
*Copy the "*.hosts.neosys.com.pfx" certificate saved in d:\hosts\certificates on win3 to the server. (password to be used is present in a text file in the same folder) | |||
*Click on Sites > Properties > Directory Security > Server certificate. Follow the steps in the wizard to import/bind the certificate to port 4430. See [https://support.microsoft.com/en-us/kb/816794 Installing imported certificate in Windows 2003 IIS] for detailed steps to import. | |||
=== Creating multiple HTTPS web sites on NEOSYS hosted server === | |||
All clients hosted on NEOSYS servers use the same IP address but unique HTTPS port numbers starting from 4431 onwards. The unique port number should be one greater than the highest port number available on the server under IIS manager -> NEOSYS ->Sites. | |||
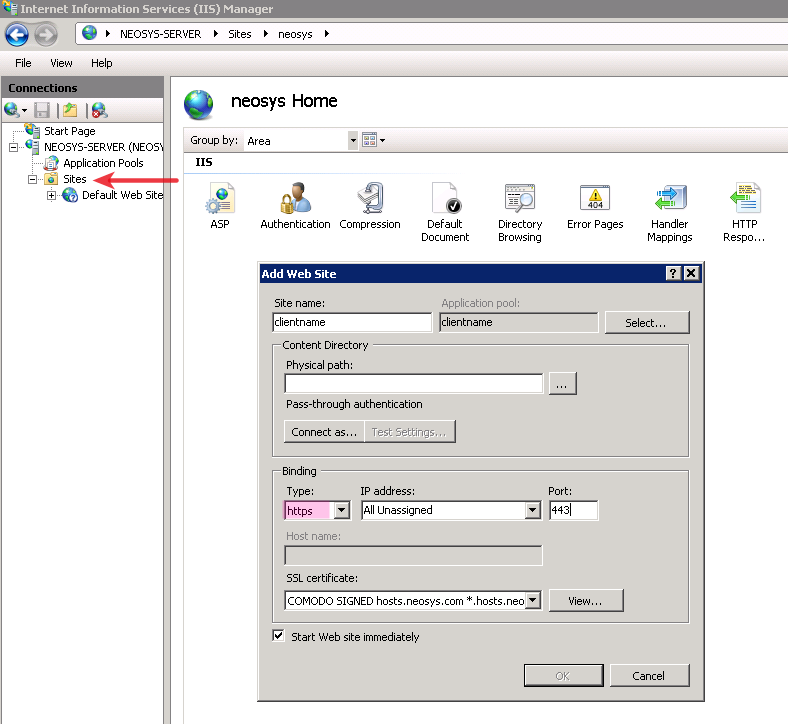
*Click on Sites > Client Web Site > Bindings. In the Bindings section - click on Add and select https, All Unassigned IP addresses, port 4430 and select the "*.hosts.neosys.com.pfx" certificate from the drop down and click OK. | |||
Since the http access is not required for any Client on NEOSYS hosted server, this step of https binding can be performed while creating the client website as shown in the screen shot below. | |||
[[image:IISwin3.png]] | |||
=== | === Steps to follow while importing certificate and why === | ||
#It MUST be imported WITHOUT OPTION TO EXPORT and | |||
#It MUST be deleted after import. | |||
It is especially important to keep pfx files off clients own servers because they are commonly directly exposed to potentially infected employees computers and/or personal devices via the corporate LAN so they may be far less secure than NEOSYS own servers which are reasonably well isolated. If a pfx file is obtained by criminal hackers, perhaps using automated tools, and the pfx password guessed, brute forced, or broken in some way, the keys contained could in principle be used against us or our clients. If the pfx file is a wildcard that supports any subdomain, then loss in one place could affect others. The chances of all this happening is probably very low but NEOSYS needs to be prepared to pass IT audits and leaving keys around will be viewed as having a culture of low security standards. | |||
== | ==Setting up HTTPS for installations with more than 1 database== | ||
In cases where there are multiple databases within the same installation, you can use the same website to access all the databases. In case the Client asks for separate domain names for multiple databases, use the same steps as explained in [[Setting_up_HTTPS#Setting_up_HTTPS_for_NEOSYS_website|Setting up HTTPS]] as the case maybe. | |||
# | |||
==Setting up HTTPS for installations where outside office access is usually restricted== | |||
During a new installation, support staff MUST import the certificate to IIS, bind the certificate to NEOSYS website (following the steps mentioned above in [[Setting_up_HTTPS#Creating_a_single_HTTPS_web_site_on_Windows_2008|Creating a single HTTPS web site]]) and test if NEOSYS can be accessed via https on the server (https://localhost:4430), so that no problems are faced in future if the client ever requests for outside access with their management's approval. | |||
Since the client management has informed that outside access is not required, close the server's port 4430 (i.e. remove 4430 from Windows Firewall exceptions). Do not remove the certificate binding in IIS. | |||
If and when https access is required by the client, this can be enabled by unblocking the server's port 4430 and instructing the client to get their IT to configure the router to port forward port 4430 for https. | |||
== Troubleshooting setup of multiple HTTPS websites == | |||
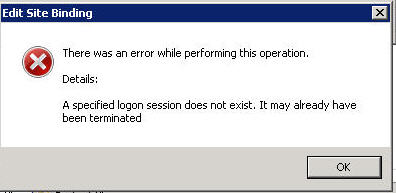
=== Error while binding COMODO signed certificate to NEOSYS website=== | |||
[[image:Test11.jpg]] | |||
A specified logon session does not exist. It may already have been terminated. | |||
If importing a certificate ONCE at the top level onto a NEOSYS controlled server with multiple web sites then you need to mark the "Allow this key to be exported" checkbox when importing the certificate to IIS. | |||
Latest revision as of 10:15, 4 February 2019
Setting up HTTPS for NEOSYS website
CAUTION: When importing certificates on servers that are not owned by NEOSYS you MUST NOT check the "allow certificate export" option otherwise anybody with access to the server can steal the NEOSYS certificate and pass off their own servers as NEOSYS certified.
NEOSYS has a very simple way of enabling https for all the clients. Every client has been set up with domain name " *.hosts.neosys.com " where "*" is the clientname.
Pre prepared certificate for *.hosts.neosys.com web sites is present on the nl10r/win3 server. The certificate is signed by COMODO and supports SHA2 security algorithm. It is portable, ensures authenticity and is widely supported. Also refer to SSL certificate
If a client's URL is not as per NEOSYS standards, but has been in use for many years, do not change the URL without a good enough reason.
Creating a single HTTPS web site on Windows 2008
To create a single HTTPS web site on Windows 2008, follow three simple steps:
- Copy the "*.hosts.neosys.com.pfx" certificate saved in d:\hosts\certificates on win3 to the server (password to be used is present in a text file in the same folder).
- Import the certificate to IIS without option to export and MUST be deleted after import. See Importing certificate in IIS for details.
- Click on Sites > Client Web Site > Bindings. In the Bindings section - click on Add and select https, All Unassigned IP addresses, port 4430 and select the certificate from the drop down and click OK.
Test the site from explorer to make sure it works.
Creating a single HTTPS web site on Windows 2003
- Copy the "*.hosts.neosys.com.pfx" certificate saved in d:\hosts\certificates on win3 to the server. (password to be used is present in a text file in the same folder)
- Click on Sites > Properties > Directory Security > Server certificate. Follow the steps in the wizard to import/bind the certificate to port 4430. See Installing imported certificate in Windows 2003 IIS for detailed steps to import.
Creating multiple HTTPS web sites on NEOSYS hosted server
All clients hosted on NEOSYS servers use the same IP address but unique HTTPS port numbers starting from 4431 onwards. The unique port number should be one greater than the highest port number available on the server under IIS manager -> NEOSYS ->Sites.
- Click on Sites > Client Web Site > Bindings. In the Bindings section - click on Add and select https, All Unassigned IP addresses, port 4430 and select the "*.hosts.neosys.com.pfx" certificate from the drop down and click OK.
Since the http access is not required for any Client on NEOSYS hosted server, this step of https binding can be performed while creating the client website as shown in the screen shot below.
Steps to follow while importing certificate and why
- It MUST be imported WITHOUT OPTION TO EXPORT and
- It MUST be deleted after import.
It is especially important to keep pfx files off clients own servers because they are commonly directly exposed to potentially infected employees computers and/or personal devices via the corporate LAN so they may be far less secure than NEOSYS own servers which are reasonably well isolated. If a pfx file is obtained by criminal hackers, perhaps using automated tools, and the pfx password guessed, brute forced, or broken in some way, the keys contained could in principle be used against us or our clients. If the pfx file is a wildcard that supports any subdomain, then loss in one place could affect others. The chances of all this happening is probably very low but NEOSYS needs to be prepared to pass IT audits and leaving keys around will be viewed as having a culture of low security standards.
Setting up HTTPS for installations with more than 1 database
In cases where there are multiple databases within the same installation, you can use the same website to access all the databases. In case the Client asks for separate domain names for multiple databases, use the same steps as explained in Setting up HTTPS as the case maybe.
Setting up HTTPS for installations where outside office access is usually restricted
During a new installation, support staff MUST import the certificate to IIS, bind the certificate to NEOSYS website (following the steps mentioned above in Creating a single HTTPS web site) and test if NEOSYS can be accessed via https on the server (https://localhost:4430), so that no problems are faced in future if the client ever requests for outside access with their management's approval.
Since the client management has informed that outside access is not required, close the server's port 4430 (i.e. remove 4430 from Windows Firewall exceptions). Do not remove the certificate binding in IIS.
If and when https access is required by the client, this can be enabled by unblocking the server's port 4430 and instructing the client to get their IT to configure the router to port forward port 4430 for https.
Troubleshooting setup of multiple HTTPS websites
Error while binding COMODO signed certificate to NEOSYS website
A specified logon session does not exist. It may already have been terminated.
If importing a certificate ONCE at the top level onto a NEOSYS controlled server with multiple web sites then you need to mark the "Allow this key to be exported" checkbox when importing the certificate to IIS.