Setting up HTTPS: Difference between revisions
m (33 revisions) |
No edit summary |
||
| Line 1: | Line 1: | ||
== Creating a single HTTPS web site == | == Creating a single HTTPS web site on nl1 == | ||
=== Creating a site in IIS === | === Creating a site in IIS === | ||
Revision as of 11:17, 23 July 2009
Creating a single HTTPS web site on nl1
Creating a site in IIS
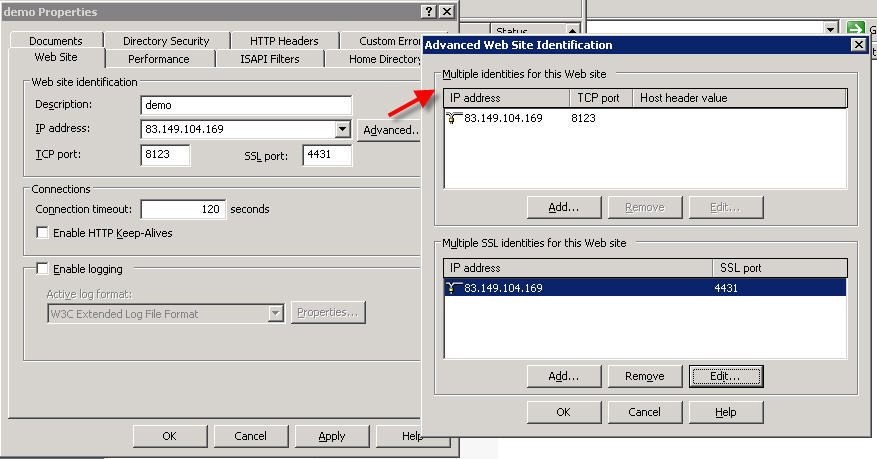
In order to run on the same port number, IIS sites need either unique ip numbers (set in tcp/http *and* ssh/https settings) or different host header values.
Therefore either the ip number has to be one of the available ones provided to neosys by leaseweb etc. or the host header value must be set to clientname.hosts.neosys.com.
The port number for tcp/http should be the neosys standard arbitrary port of 8123, not port 80 in order to prevent access via standard http. We could use various almost arbitrary ports for http since they are going to blocked by tcp/ip filtering or a firewall but it is better to know that port 8123 is the only one since IIS insists on having some port open for http.
The https options are only available after running selfssl (see below) at least once on the server.
Install ssl/https on the site.
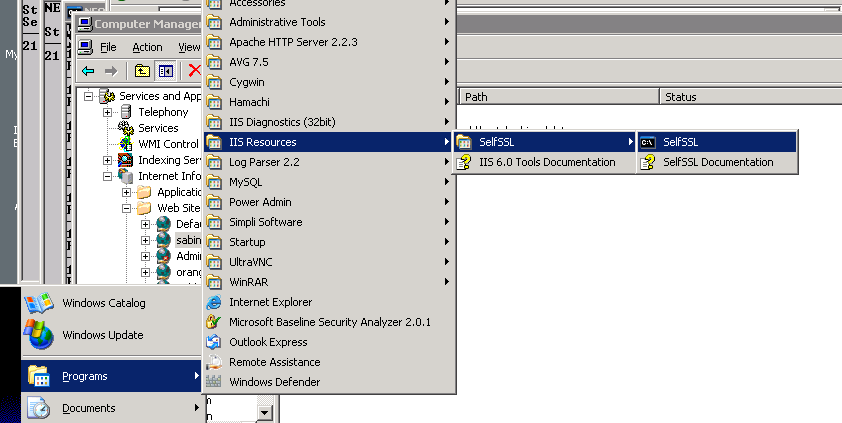
install selfssl.exe from Microsoft site (iis60rkt.exe available in neosys nl1 download folder) only the ssl utility is needed.
then
C:\Program Files\IIS Resources\SelfSSL>selfssl /v:9999 /s:866651215 /p:4430 /n:CN=clientname.hosts.neosys.com Microsoft (R) SelfSSL Version 1.0 Copyright (C) 2003 Microsoft Corporation. All rights reserved. Do you want to replace the SSL settings for site 866651215 (Y/N)?y The self signed certificate was successfully assigned to site 866651215.
/v:9999 means valid for 9999 days /s:866651215 is the site number in this case (site number is shown in IIS management screen) /p:4430 is the non-standard port number neosys uses by convention for ssl/https instead of the standard 443 /n:CN=clientname.hosts.neosys.com indicates the full domain name of the site
You probably made a mistake in the site number if you get the following message.
Error opening site metabase key: 0x80070003
Testing access to the new https web site.
Make a subdomain clientname.hosts.neosys.com
https://clientname.hosts.neosys.com:4430/neosys
If you get certificate error:
- check that the selfsll /n:CN=clientname.hosts.neosys.com matches the domain name used in IE
- install the certificate into the client computer (double click the padlock, view certificates etc)
closing all internet explorer versions and restarting is necessary for installed certificates to become effective.
Creating multiple HTTPS web sites
Bugs
SelfSSL allows only one website to have SSL at a time
IIS Diagnostics Toolkit which has fixed SelfSSL but doesnt allow full control http://www.microsoft.com/windowsserver2003/iis/diagnostictools/default.mspx
Solution
Use selfssl as follows:
- delete any existing certificate (IIS->directory security->server certificate wizard)
- create certificate for a site in selfssl following the normal procedure
- export the certificate to a pfx file (IIS->Site->directory security->server certificate wizard)
- remove the certificate (IIS->Site->directory security->server certificate wizard)
- import pfx certificate back (IIS->Site->directory security->server certificate wizard)
Continue adding sites this way and they should work perfectly fine. Just follow the sequence here for each site being added.
Certificates should be saved in d:\hosts\certificates preferably by name for easy reference otherwise by site number.
Re-installing Certificates
Sometimes due to an unknown issue, site/s stop working and hence there is a need to re-install the site certificate.
Re-installing Certificates from saved PFX files
Just do the first and last steps of the normal installation procedure.
- delete the existing certificate (IIS->Site->directory security->server certificate wizard)
- import pfx certificate (IIS->Site->directory security->server certificate wizard)
Re-installing Certificates from selfssl
Repeat the usual installation method above without missing the delete stage
If users have installed certificates in their browsers then they will have to reinstall them again to avoid the usual "certificate not trusted/matching" type problems.